Amazon web services VPC and its peering are two terms which are closely related to cloud technology. In this blog, I am going to explain what is AWS VPC and what is its peering.
Amazon Web Services VPC
Amazon VPC is termed as Amazon Virtual Private Cloud. By the help of which you can launch AWS resources into a virtual network defined by you. This virtual network is very similar to a traditional network that can be successfully operate in a data centre owned by you, along with availing various advantages of using the scalable infrastructure of AWS.
AWS VPC Peering
An amazon VPC peering is defined as a network connection situated between two different VPCs that allows you to route traffic between these two VPC's by the help of using private IPv4 or IPv6 addresses. VPC instances can communicate with each other as if they are located within the same network. You can successfully create a VPC peering connection between your own VPCs, or with an another AWS account VPC. Those VPC's which are located in different regions can also be termed as an inter-region VPC peering connection.
Lets understand the following diagram.
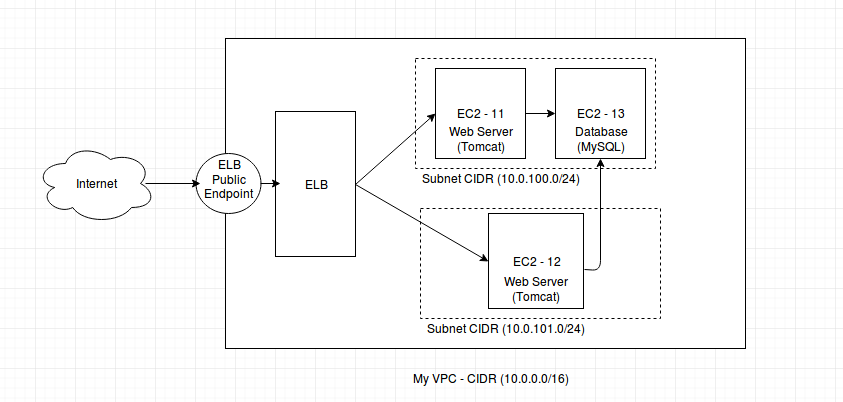
In the diagram above, I want a setup where it remains all private and inside a VPC. I have two web server instances (EC2-11, EC2-12) and one database instance (EC2-13). There is a classic Elastic Load Balancer (ELB) configured to balance the http requests to both web server instances. You can see, instances EC2-11 and EC2-13 are created in same subnet whereas instance EC2-12 has been created in another subnet. You can have them either in same or different subnets as per your requirement.
Whenever we create any instance over AWS, it creates a default VPC by itself. But we can have our own VPC and network to maintain our instances. Let's create a VPC. AWS has a good tutorial that helped me a lot in creating of a VPC. I would recommend to follow this in order to get good information. When you create a VPC, it ask for the CIDR. Provide a valid CIRD. I used 10.0.0.0/16. You can use same. Click 'Yes, Create' button to create a VPC.
Its time to create subnets. Click on subnet > Create Subnet. Select your VPC and provide CIDR range. Make sure, it should be the subset of the CIDR of your VPC. Click 'Yes, Create'. I created two subnets here with the 10.0.100.0/24 and 10.0.101.0/24. You can use same CIDR blocks. By default, AWS creates a default route tables for each subnet. You can have more entries here for example internet gateway entry to make instance publicly accessible or VPC peering to interact locally with another VPC.
When you create instance, select your VPC and assign proper subnets. As diagram show, I've been created two instance in one subnet and one in another subnet in same VPC. In my architecture, all VPCs are private and are not accessible from anywhere from internet till now as I did not added any internet gateway for subnet route table.
Question comes, how to access instances in VPC without public internet gateway associated with subnets. I've been used a VPC peering service of AWS to do so. Let 's understand the following diagram.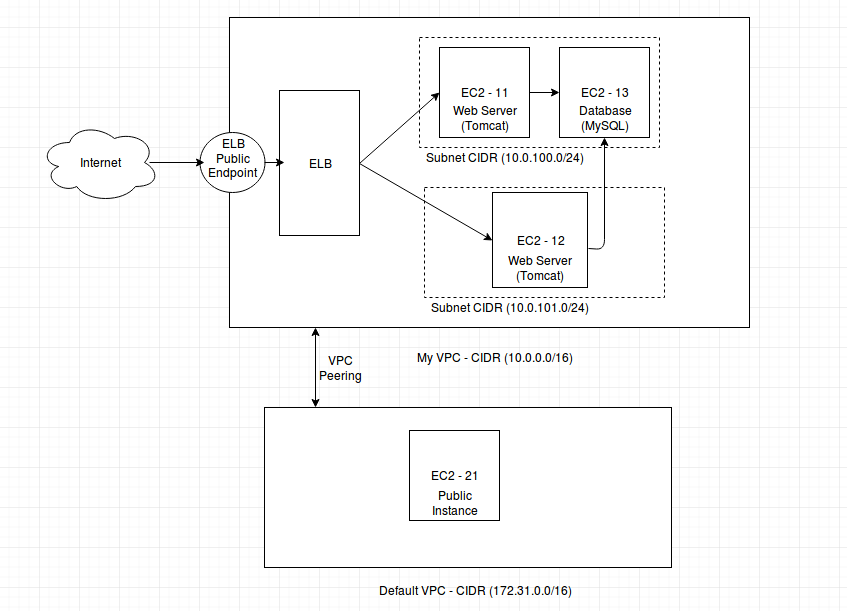
We can have another VPC or default one with a public instance (having public IP. AWS does automatically all configuration of default VPC, subnet and route table when you mark checkbox assign public IP while creating instance).
To create a VPC Peering, go to your VPC dashboard. Select VPC Peering. Define your requester and acceptor VPC. Once done, add route entry in both VPC subnets and allow ports from requester CIDR. For example if you wanna allow SSH login from Default VPC in this diagram to My VPC, add a route entry with allow 22 from source CIDR 172.31.0.0/16. This entry will let any instance of Default VPC to SSH into any instance of subnet associated with route table.
Once peering and route are done, you can access private instances in your VPC through SSH login from peered VPC instances.
I've also been configured ELB to manage EC2-11 and EC2-12. Go the the load balancer and create one classic load balancer in My VPC. Select instances that you want to manage. Make sure, your port 80/443 must open for the VPC CIDR range. ELB has its own public end point.
0 Comment(s)