When we write code and compile them,our class files are converted in to Dlls, and we assume them as safe.
But those Dll files can be used for backtracking to your code,your application logic and your secret algorithms(If you have any).
What?Are you talking real? I thought I was secured with Dlls and I implemented security too.
Yes, you implemented security but that was for your data.What about code and logic? You didn't implement anything for that purpose.
You don't need to freak out that much. You have some tools for shielding your code and the process of shielding is called "Obfuscation".
Ok. And How it's done?
There is one tool named "Dotfuscator" which ships with your Visual Studio. So let's see the steps for securing our code.
For this article I have a file named "TimeZone.dll". If I try opening this file in IL Disassembler(Will tell you about that too) it will look something like following:-
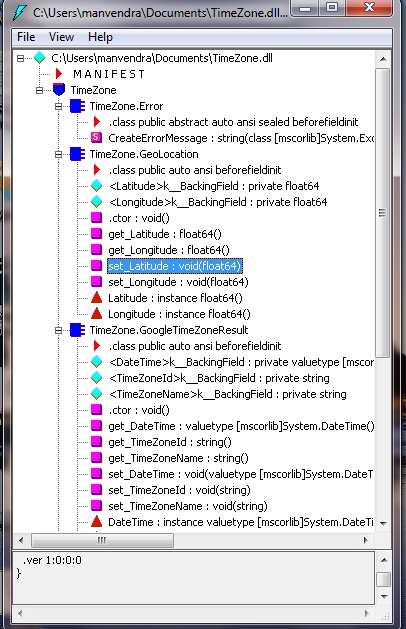 Fig 1-Dll structure exposed in IL Disassmbler
Fig 1-Dll structure exposed in IL Disassmbler
Here we can see that our method structure is clearly visible and can be guessed. So we need to obscure it in a way that it can't be guessed easily.
Open the Dotfuscator tool. You can find it in following path in your system.
"C:\Program Files (x86)\Microsoft Visual Studio 12.0\PreEmptive Solutions\Dotfuscator and Analytics Community Edition"
The drive and version may differ according to your installation path and your visual studio version. You can also find it in visual studio->tools.
After the Dotfuscator opens,you need to right click and click on "AddInput". The following pic shows the process:-
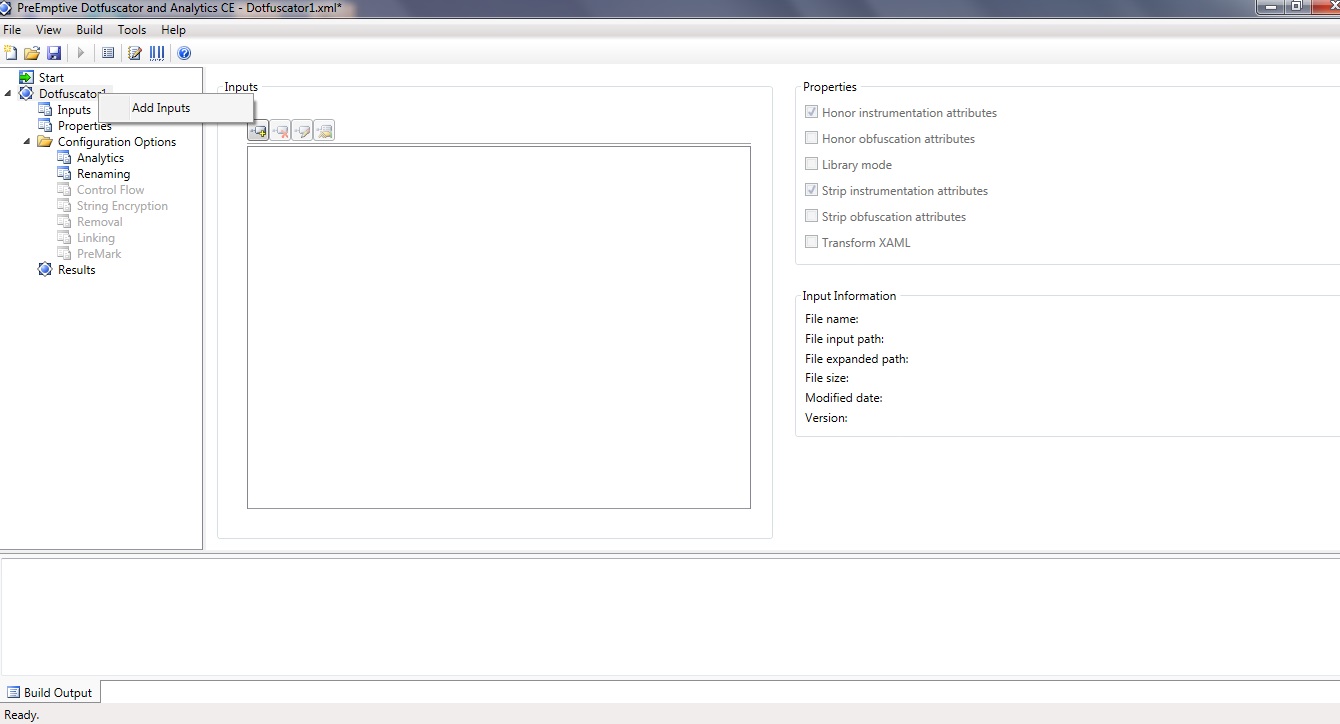 Fig 2-Dotfuscator screen
Fig 2-Dotfuscator screen
Select the desired file("TimeZone.dll" in my case) and click open file selection dialog. So the file shows here and it looks something like following:-
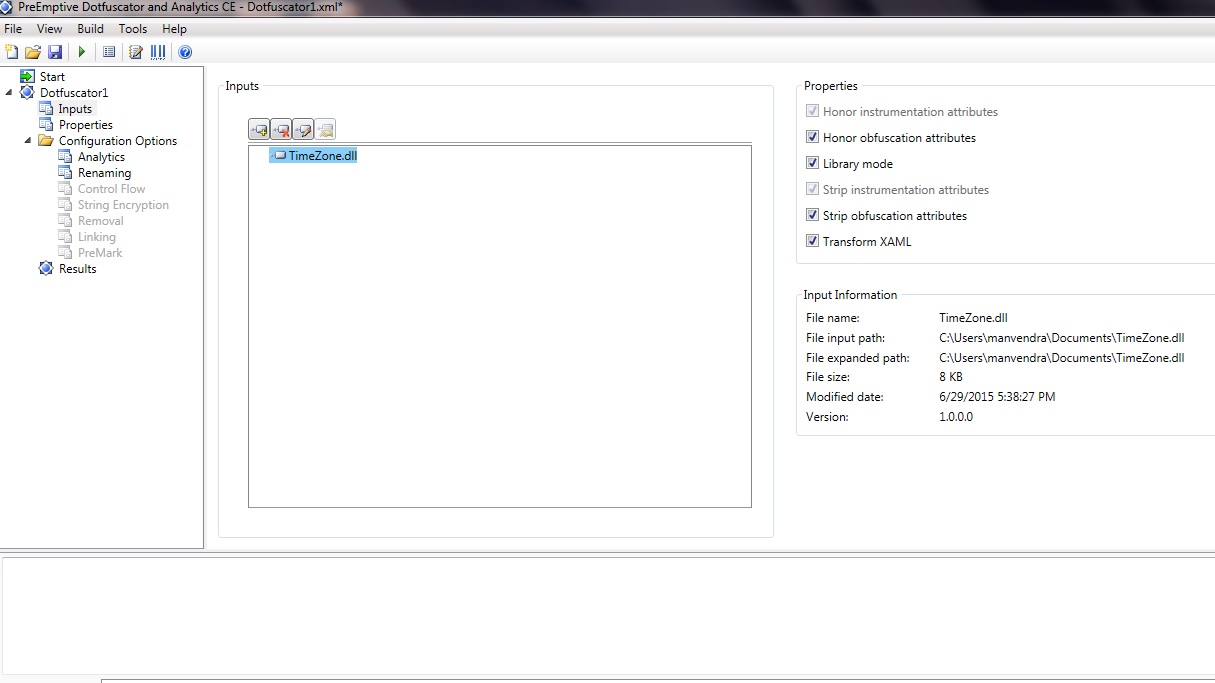 Fig 3-Dotfuscator screen
Fig 3-Dotfuscator screen
Now that you've selected your Dll,click the green arrow and start the conversion(You can see the button just below the "Build" menu option on top left).
After the process has been completed,we need to take a look at our obfuscated dll file. By default it is found in "Dotfuscated" folder (Created by Dotfuscator right where your file exists). You can change the output path to a specific one.
Now we can check the changed file and it looks something like following:-
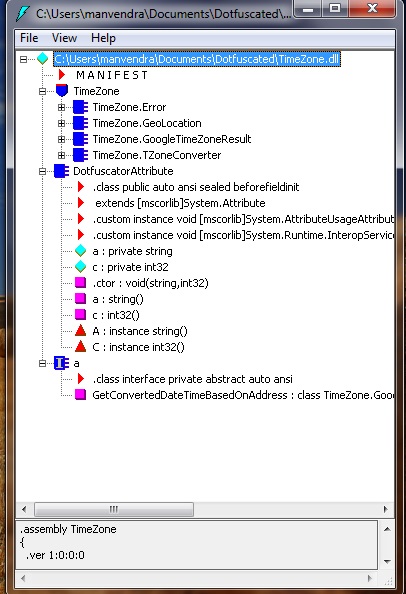 Fig 4-Obfuscated DLL
Fig 4-Obfuscated DLL
We can see that names of all of the methods or variables are changed and they provide almost no clue about the Dll functionality.
IL Disassembler
IL Disassembler is a tool which can be used to see the definition of assemblies by disassembling them. For opening it you will go to Visual Studio Command Prompt.
And then you need to type "ildasm" and press enter. The IL Disassembler will open. Now you can open any Dll file in it.
So any obfuscating software makes the code more secure or less secure than others available in market but they can't make it 100% impenetrable.The obfuscation should be your last line of defense that means you should implement other means of code security like secure servers(in case of web or client server system) or user permissions to your installation folder(can be configured when you are creating the setup of application) when your application is one standalone systems etc.
Happy Coding:-)
0 Comment(s)