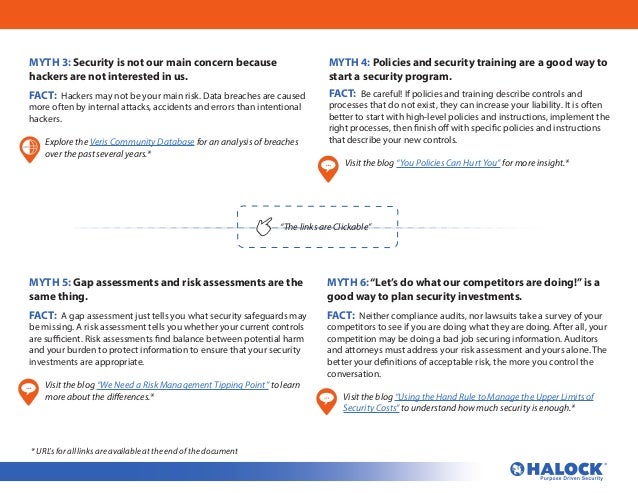
The world created by computers and networks may be considered “virtual reality,” but that doesn’t mean their use in the business world should be subject to different rules, especially when it comes to security and compliance. On many occasions, firms treat their risk management when it comes to their networks and computers as separate from the common-sense dictates that rule their decision-making in the “real” world. Some firms tend to believe that digital security and compliance should operate under a different set of rules, and that leads to confusion as well as serious risk. The truth is that while there is advanced technology at play, digital security and compliance should be ruled by foundational, old-fashioned common business sense, the same as any other types of risk management.
Many businesses apply this type of thinking when it comes to risk management in the digital realm and this has given rise to numerous myths. These myths can lead to companies making some dangerous and misinformed assumptions about how they should approach digital security and compliance. For example, too many firms believe they don’t need to worry about their digital security because they are not prime targets for hackers. However, this can be the same as leaving your sensitive equipment outside in the rain because you’re not worried about thieves. Data breaches can happen just as easily through internal errors and accidents as they can due to external factors such as hacking or criminal agents using ransomware, and security measures protect against these as well.
The following guide points out 10 of the most common myths organizations have when it comes to cyber-security risk management and compliance, as well as the facts. Knowing the difference between the two may be critical for your company as you navigate the often high-level nature of today’s cyber-security and compliance landscape. It may seem as if your computer networks exist in a different reality from the rest of your organization, however, the reality is that the same real-world principles apply to them.




Created by information security consulting company Halock Security Labs
0 Comment(s)